HOW IT WORKS
GoAnywhere Managed File Transfer
Looking to centralize and secure file transfers with ease, streamline manual processes, and achieve compliance with data security standards? We can help with our enterprise secure file transfer solution.
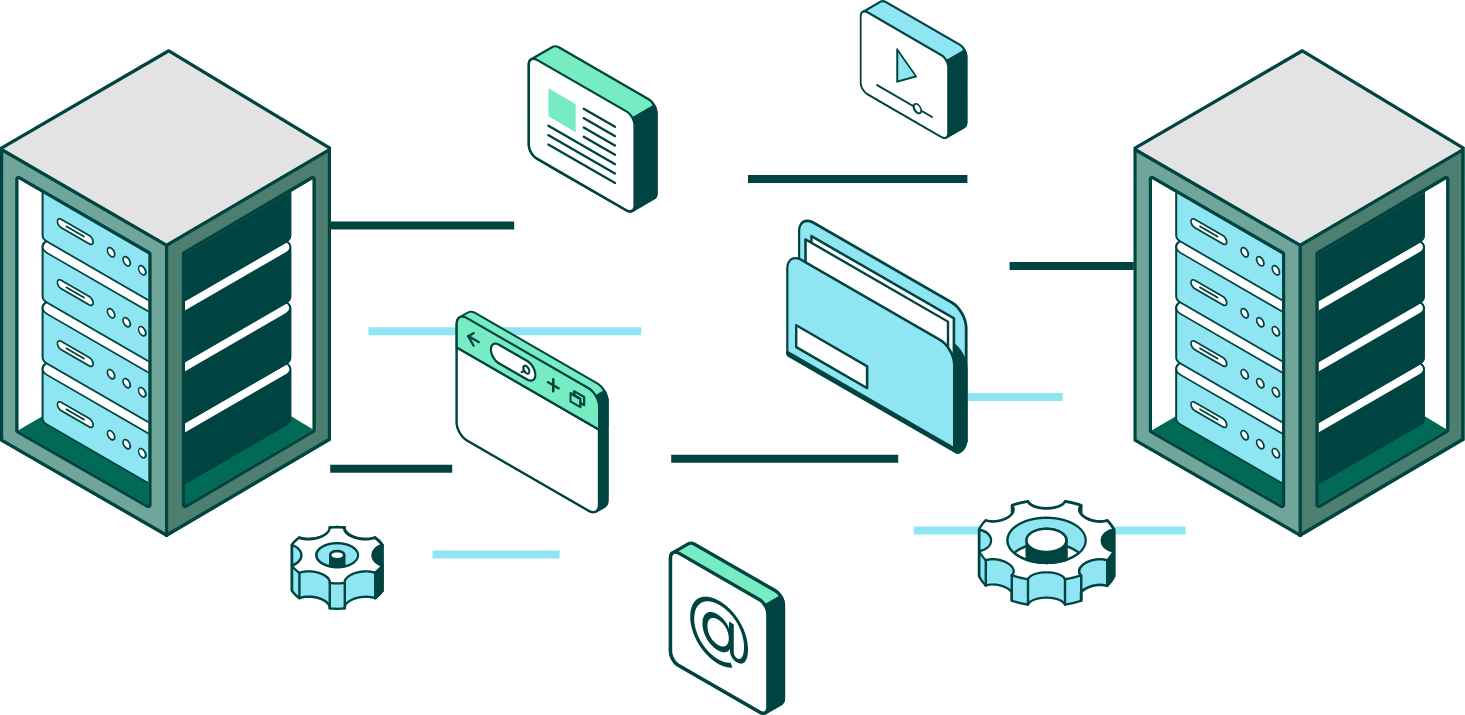
BATCH FILE TRANSFER AUTOMATION
Move Files Automatically
Replace your manual processes and legacy scripts with a better way to automate secure file transfers. Deploy workflows you design and schedule future transfers to get files where they need to go, fast.
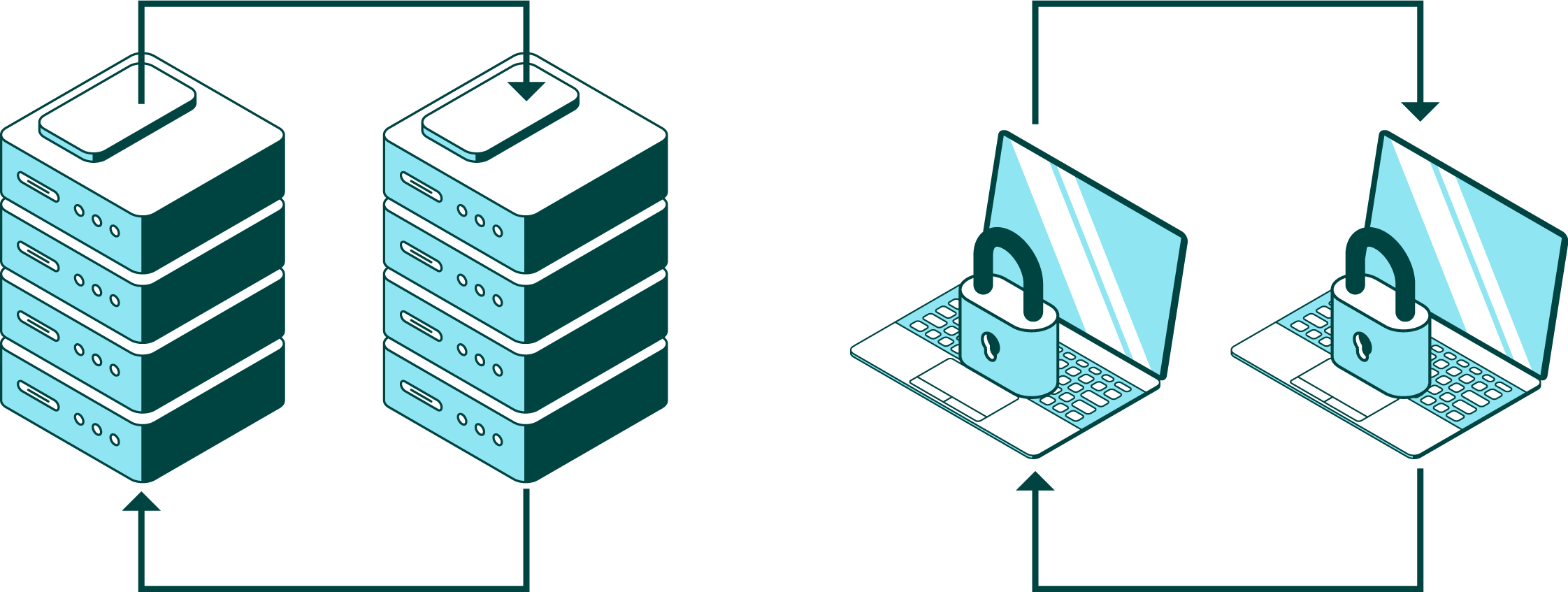
FILE ENCRYPTION, SECURITY, & COMPLIANCE
Protect Your Data with Enterprise Secure File Transfer Software
Safeguard file transfers and meet all your IT security and compliance requirements using modern encryption technology and authentication methods. GoAnywhere provides enterprise-level security features to protect your files from internal and external risks and helps organizations and professionals alike comply with regulations, standards, and technologies.
FAST FILE TRANSFER
Send Large Files, Fast.
FileCatalyst can transfer your files of any size or format at speeds up to 10 Gbps – that's hundreds of times faster than FTP. And this UDP-based solution does so even in environments experiencing latency or packet loss. Get secure, reliable, and truly accelerated delivery from anywhere in the world.

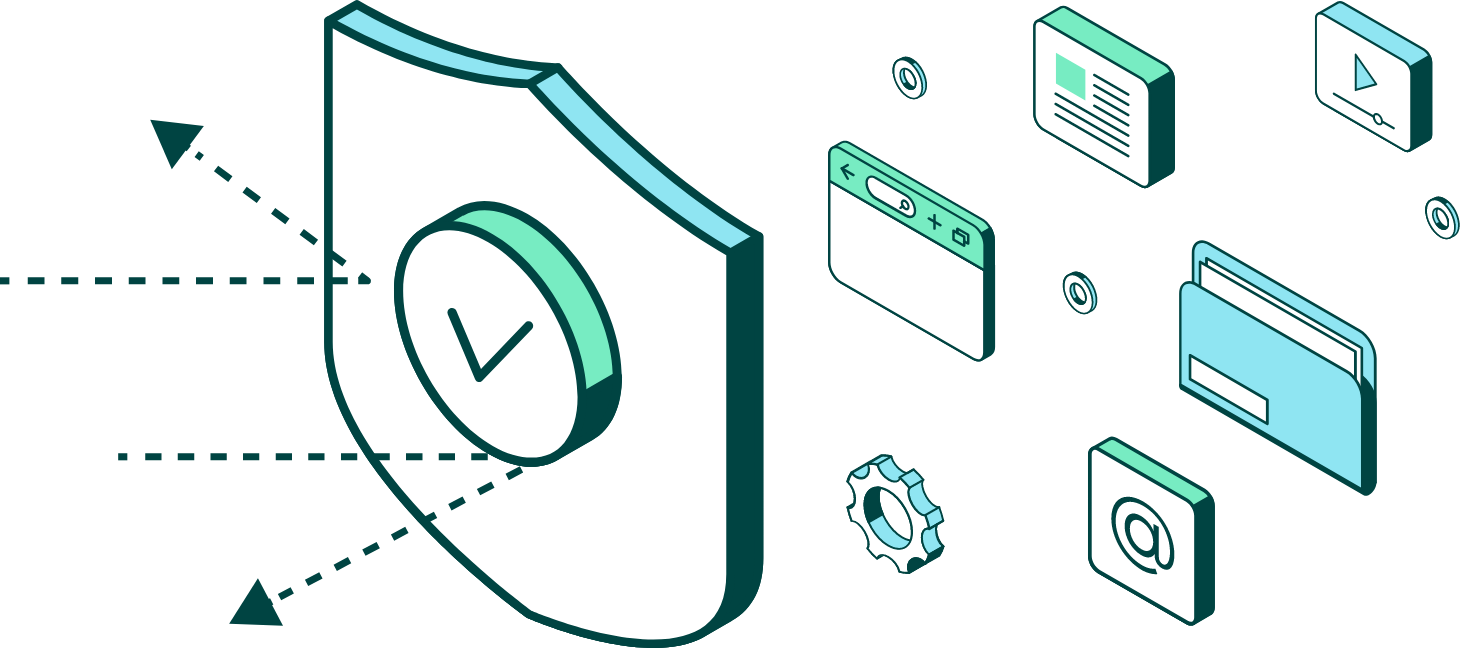
POWERFUL BUNDLES
Enhance File Transfer Security
Want to protect all incoming files from malware? Done. Need to encrypt and control access to your most sensitive files wherever they travel? No
problem. GoAnywhere bundles for threat protection and secure collaboration make file transfer even more secure.
CLOUD FILE TRANSFERS
Implement MFT in the Cloud
GoAnywhere MFT supports secure file transfers in the cloud, either your cloud platform or our MFTaaS option. Whether deployed on AWS, Microsoft Azure, or another cloud computing platform, you'll rest easy knowing your data is secure no matter where it resides.
COLLABORATION
Achieve Secure User-to-User File Sharing
Easily share files with colleagues, trading partners, and third-party vendors via GoAnywhere's secure collaboration features. Users can access authorized files and folders through a web browser, send ad-hoc emails, gather information with custom forms, and more.
Explore Collaboration Features >
Testimonials
See Why Leading Organizations Choose Us for Their MFT Needs


A Key Part of Fortra
GoAnywhere is proud to be part of Fortra’s comprehensive cybersecurity portfolio. Fortra simplifies today’s complex cybersecurity landscape by bringing complementary products together to solve problems in innovative ways. These integrated, scalable solutions address the fast-changing challenges you face in safeguarding your organization. With the help of the powerful protection from GoAnywhere and others, Fortra is your relentless ally, here for you every step of the way throughout your cybersecurity journey.
Secure Your File Movement with GoAnywhere
Download a free 30-day trial and see if GoAnywhere is the right solution for your organization.
Secure Your File Movement with GoAnywhere
Download a free 30-day trial and see if Fortra's GoAnywhere is the right solution for your organization.