What do real end-users say about their managed file transfer (MFT) software vendors?
To provide a holistic review of the file transfer landscape, Info-Tech Research Group evaluated the most popular managed file transfer software and vendors in the MFT market.
This detailed analysis includes:
- Managed file transfer software comparison and review of top vendors including head-to-head comparisons of GoAnywhere MFT, Progress MOVEit MFT, IBM MFT, and more.
- Vendor satisfaction leaders in areas including ease of implementation, product strategy, and vendor support.
- Leaders in product feature satisfaction in areas such as encryption/decryption, file transfer, and multi-platform support.
Download the report to compare and determine which managed file transfer software is right for your organization, or find the right MFT alternative if your current solution isn't meeting your needs. Fortra MFT solutions hold two out of the top three spots for managed file transfer solutions.
Get a Sneak Peek of the MFT Review Data Quadrant
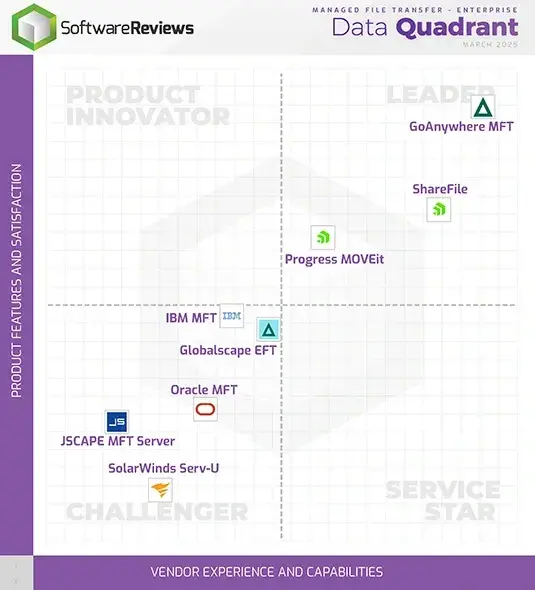
The latest Managed File Transfer Data Quadrant comparing MFT vendors, including GoAnywhere MFT, Progress MOVEit MFT, and IBM MFT.