
Since moving to Electronic Health Records and modern EHR technology, the healthcare industry has taken great strides to enhance patient care, internal workflows, and business-to-business communication. These improvements bring organizations closer and closer to full integration with others in the industry; a goal that will, once fully achieved, help streamline the data sent between patients, payers and providers.
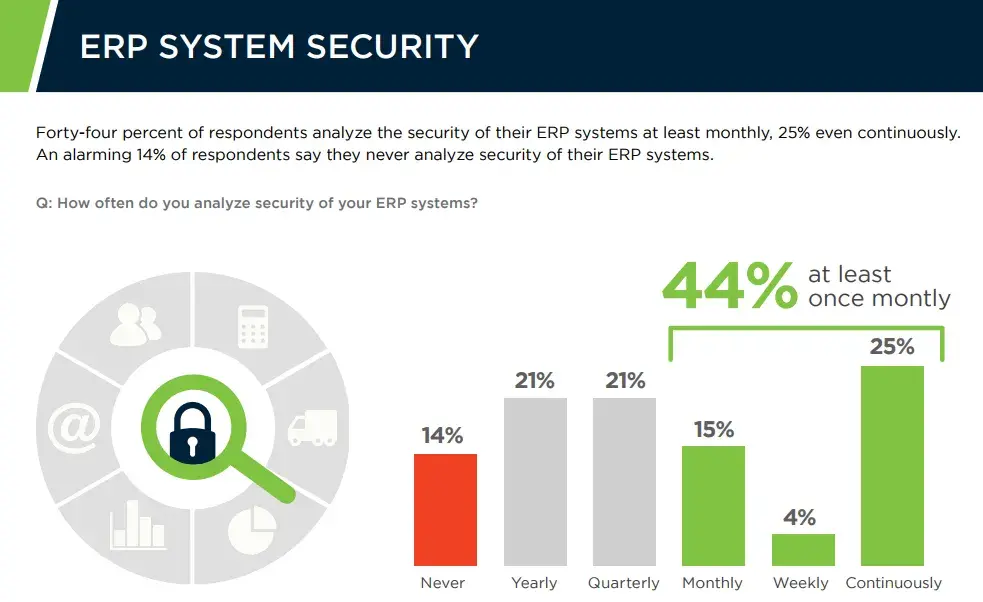
But this change toward interoperability isn’t without risk. Though EHRs are beneficial, they can unintentionally compromise the safety of sensitive patient information. Enterprise Resource Planning (ERP) software, which is used to facilitate and improve communication between organizations, is also vulnerable—sadly, it often lacks proper auditing, with 14% of polled users admitting they’ve never analyzed the security of their ERP systems.
Healthcare providers need to ensure that the security surrounding EHRs and EHR software remains top-notch to prevent gaps in cybersecurity, especially ones that can lead to leaked patient information and identity theft.
Are your Electronic Health Records secure, or are they vulnerable? Here are the most common cybersecurity risks around EHRs and EHR software that healthcare providers run into.
Manual Management of Security
If you implement and maintain your cybersecurity manually, you may not be operating your organization or protecting your EHRs at optimum security levels. Manual work relies on human precision, technical understanding, and incredible attention to detail, all of which burn up precious resources and leave room for error—like missing small anomalies in the system or overlooking compliance requirements.
Manual security and compliance also put the burden of tracking and identifying unauthorized user and EHR changes on a few people who may not notice something happening in a sea of activity. Unfortunately, in this day and age, custom scripts and programs are not enough to satisfy standard compliance requirements either.
Outdated Systems
When EHR software first came out, with the government urging healthcare providers to move from paper to electronic records, many organizations didn’t have the pieces in place for its implementation. Trend Micro writes that because of this rush, “healthcare technology is often outdated and insecure, leaving systems vulnerable to attack vectors long after they are discovered.”
Are all your systems, hardware, and interfaces up-to-date? EHR software connects multiple facets of technology in your organization, allowing “systems as diverse as EHR portals, printers, nurse’s stations, [and] active medical devices … [to] freely communicate with each other,” reports research from Harvard University. What’s more, “healthcare facilities make extensive use of legacy systems. In fact, numerous hospitals still rely on devices that have reached their end-of-life or that are no longer supported,” they add. What’s the bottom line? If even one of those systems are outdated or insecure, including that corner printer staff rarely use, a well-aimed cyberattack could infiltrate patient data.
Ransomeware Attacks and Limited Data Backups
The frequency of cyberattacks is rising. In fact, it seems like everywhere we look, we’re seeing one hit some industry or another, paired with soul-crushing statistics that make us frustrated, worried, … and weary.
For healthcare providers in particular, ransomware has become a real concern. In 2016, ransomware accounted for 72% of healthcare malware attacks. Why? EHRs are an easy target. Because they’re stored electronically, they can be held at ransom until the organization pays the hackers to unlock their maliciously-encrypted data. And until that time—which could be anywhere from hours to days—there’s a good chance patient data can’t be accessed at all.
While battling ransomware requires proper preventative measures like employee training, strong firewalls, secure systems, and impossible-to-crack user credentials, you can protect patient data during a breach through proper file encryption and periodic backups.
EHR backups are one of HIPAA’s many compliance requirements; if you aren’t creating or maintaining copies of your database and storing them offsite, make that a priority for your organization. It’s easy to hope you’ll never be victim to a ransomware attack. It’s even easier to believe you’ll slip under the radar, unnoticed. But without proper backups (and a data breach response plan), a successful attack will hurt your bottom line, cost you hours of work resources, and compromise patient data.
Problems with EHR Interoperability
When looking for vulnerabilities in your organization, you should review your EHR software and the software of other healthcare partners you communicate with. A particular problem many have run into since the implementation of EHRs is a lack of decent EHR interoperability. This describes the issue of collaboration between systems, both internally and externally.
According to EHR Intelligence, “research shows that many [collaborative] tools can’t easily exchange health data with one another.” If a patient requires treatment from multiple providers, like a regular physician, a specialist, and a physical therapist, their data and history will need to be sent from one office to another, and sent seamlessly. Unfortunately, EHR Intelligence adds, “as the industry stands now, that capability is limited.”
If your EHR software has difficulty linking to other systems or software, there’s yet another opening for hackers to compromise patient information. Though smoothing out the kinks in EHR interoperability may not be something you can do, protecting your data is completely under your control. Make sure every file transfer, no matter where it’s headed, is encrypted with secure, standard network protocols like SFTP, FTPS, SCP, and HTTPS. When data’s at rest, encrypt individual data with Open PGP and AES encryption standards.
Do you need help securing your EHRs and EHR software? Learn more about the healthcare industry, and how GoAnywhere can help you meet HIPAA compliance requirements and secure your file transfers, on our healthcare industry page.
