What is SFTP?
SFTP, which stands for SSH File Transfer Protocol, is a secure file transfer protocol used to secure and send file transfers over secure shell (SSH). This SFTP connection, as a network protocol, implements AES, Triple DES, and similar algorithms to encrypt files as they transfer between systems.
How Does SFTP Work?
SFTP works over the Secure Shell (SSH) data stream to establish a secure connection and provide organizations with a higher level of file transfer protection. This is because SFTP uses encryption algorithms to securely move data to your server and keep files unreadable during the process. Authentication prevents unauthorized file access during the operation. Read more on how the SFTP connection works >
SFTP Encryption
SFTP uses AES, Triple DES, and similar algorithms to encrypt files during data transfer. SFTP uses a single port number (port 22) to establish a secure connection and encrypts both authentication information and the files being transferred. Read more on SFTP encryption >
Authentication Methods
An SFTP server requires trading partners to authenticate in one of two different ways. They can either prove their identity with a user ID and password (this information is encrypted over the SFTP connection rather than sent over plain text) or validate with an SSH key. Users can also use two-factor authentication and a combination of SSH key and password. These types of authentications prevent imposters from connecting to the SFTP server.
There's some debate on whether SSH keys or passwords are better at protecting and validating company SFTP servers. For a full comparison of the two authentication methods, read Are SSH Keys or Passwords Better for SFTP Authentication?
What is Secure FTP?
File Transfer Protocol (FTP) is a network protocol used to transfer files between clients and servers. Secure FTP solutions take the basic function of FTP – file transfers – and makes it more secure. Since FTP is not secure in and of itself, it is often secured with SSL/TLS (to become FTPS) or replaced with SFTP (SSH File Transfer Protocol) solutions.
SFTP vs. FTP
The biggest, and one of the most crucial differences, between FTP and SFTP is the fact that one is encrypted (SFTP) while the other is not (FTP). SFTP is a much more secure protocol compared to FTP, considering that when files are being sent and received using "standard" FTP, they are done so in an unencrypted manner. Read more >
When to Use FTP
FTP still exists today but, while a surprising number of people still use it to move files from point A to B, it is no longer the best way to ensure the secure transfer of files.
FTP should only be used when you are exchanging or sending files that aren’t sensitive in nature. If standard FTP is running on your organization’s server, you should disable it as soon as possible; FTP is over 30 years old and isn’t meant to withstand the modern security threats we face today. FTP is not encrypted, and it lacks privacy and integrity, which makes it easy for a hacker to gain access and capture or modify your data while it’s in transit. More on when to use FTP >
Why do users continue to employ FTP? It’s often free, and open-source FTP software does not require much digging to find.
Why Shouldn't You Use FTP?
- Authentication. FTP isn’t authenticated, meaning information including your ID and password are sent as plain text, rather than encrypted. FTP as a whole is not encrypted, leaving your information unprotected.
- Maintenance. FTP was never intended to be used forever, and other file transfer protocols have sprung up to replace FTP and protect data.
- Compliance. FTP is not robust enough to ensure the secure transfer of files. More specifically, it does not meet many of today’s business and compliance requirements. New data security standards and regulations stipulate the minimum requirements for secure data transfers – and FTP is not one of them.
Should You Replace Your FTP Scripts?
As cybersecurity is increasingly top-of-mind for organizations, many are moving away from FTP to file transfer tools that are secure, easy to use and maintain, and include more features. The benefits of replacing legacy scripts and FTP include gaining the ability to centralize your workflows, automating your data movement, easily meeting compliance regulations, and overall securing your transfers. Keep Reading >
How to Secure Your FTP Server
- Place your servers behind a gateway. Many organizations store their FTP servers in the DMZ, a public-facing segment that is easy to attack. Using an enhanced reverse proxy like a DMZ Secure Gateway keeps files and credentials in the private network, rather than opening inbound ports.
- Implement IP Blacklists and Whitelists. An IP blacklist allows you to deny system access to a range of IP addresses, either temporarily or permanently. If your trading partners use fixed IPs, you can whitelist their specific IP addresses.
- Implement file and folder security. Limit folder access to only the essentials. Encrypt files at rest, especially if they’re stored in the DMZ, and retain files on the FTP server only as long as needed.
- Lock down administration. Restrict admin duties to a limited number of users and require to use multi-factor authentication. Avoid easy-to-guess admin user IDs like “root” or “admin,” and protect passwords by storing them in an AD domain or LDAP server.
More best practices: 10 Essential Tips for Securing FTP and SFTP Servers >
See More SFTP Benefits
Move beyond FTP and learn how to secure and manage your file transfers.
Alternatives to Secure File Transfer Protocol
Back in the day, File Transfer Protocol (FTP) was the go-to method for sending files. Now, there are more options, all of which improve on security including FTPS, HTTPS, AS2, and MFT.
SFTP vs. FTPS
Two mainstream protocols available for secure file transfers are Secure Shell (SSH) File Transfer Protocol (SFTP) and File Transfer Protocol over SSL/TLS (FTPS). Because SFTP and FTPS implement strong algorithms like AES and Triple DES to encrypt any data transferred, they both offer a high level of protection. Read more >
| SFTP | FTPS | |
|---|---|---|
| Port for secure FTP | Uses only port 22. | Uses multiple port numbers; one for the command channel, and an additional port on the data channel for every file transfer request or directory listing request. |
| Authenticating connections | Choice to use a user ID and password to connect to an SFTP server or to use SSH keys with or instead of passwords. | Uses TLS/SSL to encrypt server connections and X.509 certificates to authenticate the connections. |
| Authentication | Algorithms like AES and Triple DES are used to encrypt transferred data. | |
| Speed | Control and synchronization packets are sent on the same channel as data packets, which may cause SFTP to be slightly (but not significantly) slower than FTPS. | Was designed to be more speed-friendly, with the control and data channel running asynchronously. |
| Implementation | Considered the easiest secure FTP protocol to implement. | Can be difficult to patch through a tightly-secured firewall. |
SFTP vs. AS2

AS2, part of the Applicability Statement family, is one of the top file transfer protocols for Electronic Data Interchange (EDI) information. AS2 uses a secure TLS layer to secure data in transit and gives users the option of using a digital certification for authentication.
Unlike SFTP, AS2 has a feature that makes it unique: it allows users to request a Message Disposition Notification (MDN), also known as a receipt, that alerts the sender once the message has been received and decrypted by the recipient. For a deeper dive into the differences, read Which is Better: AS2 vs. SFTP?
SFTP vs. SSH
Although they are both used to transfer information securely, unlike SFTP, SSH is able to exist on its own. Typical applications for SSH are remote command-line, login, and remote command execution. SFTP is the file transfer protocol that provides secure file access, file transfer, and file management over a reliable data stream.
SFTP vs. MFT (Managed File Transfer)
By nature, SFTP and MFT solutions both work to protect data in transit. They both authenticate trading partner connections with a combination of user IDs, passwords, or keys, and they both help satisfy strict requirements for data security laws like PCI DSS, HIPAA, and the GDPR. However, MFT solutions offer more functionality than just an SFTP connection.
- Flexibility: secure managed file transfer supports most file transfer protocols, including AS2, HTTPS, SFTP, and FTPS, to secure the exchange of information between users
- Automation: Cut down on user errors, reduce or eliminate the need for scripts, and reduce manual time
- Compliance and auditing: Track file transfer activity to maintain compliance with regulations and privacy laws
- Clustering: Meet high volumes of file transfers by distributing processes across multiple systems for load balancing
- Key and certificate management: Import, export, and monitor SSH keys and SSL certificates, and receive notifications ahead of expiration dates
- Centralization: Manage and monitor all aspects of your file transfers from one dashboard
Managed file transfer includes an extensive list of security features, including encryption for files in motion and at rest, and supports workflow automation, file transfer monitoring, notifications, and auditing. Enhance your team’s productivity in multiple ways while keeping security at the forefront.
Read more on the differences between SFTP & MFT >
SFTP Automation
One of the largest differences between SFTP and an MFT solution is the ability to automate file transfer processes. MFT solutions provide SFTP automation, allowing IT professionals to streamline their organization’s exchange of data over a secure SFTP connection. Automation can improve multiple transfer processes: projects and tasks to run, file monitoring, data exchanged with cloud or web services, recurrent file transfers, and file encryption.
SFTP vs. HTTPS
HTTPS (Hypertext Transfer Protocol Secure) is a secure version of HTTP, offering certificate authentication, encrypting a website’s inbound traffic, and using a TLS encryption layer for data integrity and privacy. HTTPS protects the identity, account details, payment information, and other sensitive details on behalf of web visitors.
SFTP vs. TFTP
Like FTPS and SFTP, Trivial File Transfer Protocol (TFTP) is based around FTP technology but is a completely different protocol. Like FTPS and SFTP, the TFTP protocol does allow for file transfers but uses a completely different approach to how files are transferred.
As you might have gathered from the name, Trivial File Transfer Protocol is a stripped-down transfer protocol: it can only be used to send and receive files. TFTP is best used in cases where you know the exact file and its precise location and don’t require any security or encryption when sending or receiving that file. With TFTP, user authentication and directory visibility are not possible, and TFTP allows anyone who knows the right pathing to upload and download files.
SFTP vs. SCP
SCP is a more simplified, efficient transport algorithm, making it faster than SFTP, especially on high-latency networks. SCP does not, however, provide the ability to list directories, rename files, or other file management capabilities. It also does not resume transfers if there are connectivity issues.
Read more about SFTP vs. SCP >
Secure FTP FAQs
Secure File Transfer Protocol (SFTP) Software
SFTP Client
A file transfer client gives you the ability to connect to a server and upload files to or download files from that server. SFTP can be run natively from the shell on most machines, allowing users to transfer files via SFTP from the command line between computers. Graphical secure FTP clients have user interfaces but still require programmer time to make custom scripts, run commands, manually audit, and potentially use add-on tools (like PuTTYgen).
MFT solutions are among the most robust secure FTP client software solutions. They can be deployed on-premises or in the cloud and give you the ability to streamline and safeguard traditional SFTP data submissions with features like automation, status notifications, transfer resume, and integrity checks.
SFTP Servers
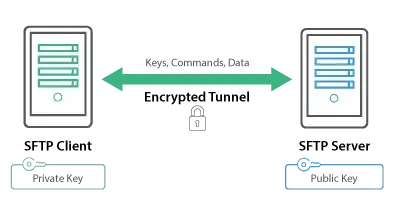
Organizations can securely exchange sensitive data over a network with an SFTP server.
With GoAnywhere MFT, data integrity and security is assured by using an encrypted tunnel created between the SFTP server and trading partners. This helps to protect all that flows over the connection – data, user IDs, passwords, and commands.
Trading partners can exchange files securely with your organization using SFTP (SSH File Transfer Protocol) and SCP (Secure Copy) protocols. They can also authenticate with both passwords and SSH key authentication.
SFTP Server Features
- Robust security and granular permission controls
- Can be installed in the private network without opening inbound ports, when paired with GoAnywhere Gateway in the DMZ
- Highly scalable with no restrictions on the number of trading partners
- Allows only strong NIST-certified encryption algorithms when in FIPS 140-2 Compliance mode
- Support for multiple listeners with configurable port numbers
- Multiple authentication methods; database, Active Directory (AD), LDAP and IBM i
- Event triggers to automatically process files or send email notifications
- Support for client requests to resume file transfers
- Configurable settings for maximum number of sessions, maximum login failures and idle timeouts
- ZLIB compression to reduce bandwidth requirements
- Ability to accept or reject files with certain extensions
Free SFTP Software vs. Enterprise
Free SFTP software an inexpensive way to occasionally exchange files, providing basic functionality for simplistic needs. Enterprise-level SFTP software typically comes with robust security, automation, auditing and reporting functionality that streamline the transfer processes across an organization.
As you evaluate your needs against your budget, weigh these pros and cons against the ones for an enterprise-level SFTP solution to better determine which will fit your organization’s file transfer needs.
Why Use Secure FTP Software?
Secure FTP solutions, including GoAnywhere MFT protect sensitive file transfers with strong encryption and authentication methods. GoAnywhere's support for the three secure FTP standards (SFTP, FTPS and SCP) creates encrypted tunnels between client and server systems.
How to Connect to GoAnywhere’s SFTP Server with a File Transfer Client
Connecting to SFTP with GoAnywhere MFT involves selecting the protocol, entering the server details, setting authentication methods, and testing the connection. Once established, you can securely transfer files as needed. Of course, you can refer to the GoAnywhere MFT documentation for more details.
- Launch the file transfer client application.
- Create a new connection
- Select SFTP as the protocol
- Enter connection details (Hostname, Port 22, username, and password)
- Set up authentication via password or public key authentication:
- Configure any additional settings such as encryption, proxies, or timeouts.
- Test the connection, verify settings are correct, and that you can successfully connect to the SFTP server.
- Save the connection configuration for future use
- Transfer, upload, manage, or download files on the SFTP server within the file transfer software interface.
Learn More About the Secure FTP Solution Components in GoAnywhere MFT
Secure FTP Software Features At a Glance
Try SFTP Today
Looking for the best FTPS, SCP, or SFTP server for your file transfer needs? Learn how GoAnywhere MFT can help you achieve your file transfer goals with secure, encrypted FTP clients and servers for Windows, Linux, IBM i, and other platforms.
SFTP Deployment Options
Cloud
SFTP itself isn’t necessarily cloud-based, but it can be used to transfer data to, from, or within cloud-based environments. You can also deploy an SFTP client or server within your preferred cloud platform. Your server, whether already in the cloud or on-premises, serves as the “tunnel” for all transfer activity.
A few SFTP benefits for cloud-based file transfers:
- Use a hosted server, like Azure, AWS, or VMware to achieve cloud SFTP
- Deploy an on-premises SFTP solution and transfer data to and from the cloud
- Deploy an SFTP solution in your cloud environment to transfer data
- Use a SaaS solution that includes built-in secure file transfer protocols
Other Operating Systems
SFTP software can be deployed on-premises as well as in the cloud, including on platforms such as AIX, IBM i, Linux, Windows, and Mac OS.
DMZ Secure Gateways
Traditionally, SFTP servers have been installed in the DMZ (or public facing) segment of the network since organizations were fearful of opening inbound ports into the Private (internal) network. Keeping the SFTP server in the DMZ, however, has posed several problems. The primary issue is that files have to be stored in the DMZ when they are dropped off by partners, or otherwise staged temporarily for pickup. Those staged files have a higher risk of being accessed by hackers since the DMZ is more exposed to the Internet.
An approach that is quickly gaining in popularity is to implement a gateway component in the DMZ. The gateway will serve as an enhanced reverse proxy which does not require inbound ports into the private network. At startup time, the SFTP server will establish a special control channel with the gateway, which is kept alive continuously. When partners connect to the gateway, it will make requests over the existing control channel to the SFTP server. The SFTP server will then open any data channels needed back through the gateway to service the trading partners. The whole process is transparent to the trading partners. No data is ever stored in the DMZ since it is simply streamed through the gateway. Read more >
Protect your files by keeping them out of the DMZ. Keep your file servers securely in your internal network:
- Secure inbound ports to your network.
- Share files with trading partners and clients without storing confidential documents in the DMZ.
- Enhance the security of any environment or operating system.
Achieve More with GoAnywhere MFT
GoAnywhere MFT offers more than just SFTP benefits. Expand the security, functionality, and flexibility of your solution with a selection of licensable modules:
- Advanced Workflows: Achieve secure FTP automation. Define how your file transfers and processes are configured.
- Secure Folders: Grant trading partners and customers access to authorized files and folders.
- Secure Mail: Send encrypted messages and files through GoAnywhere's web client or Microsoft Outlook.
- Cloud Connectors: Achieve easy connectivity, including centralization and automation, with popular cloud and web applications like Box and SharePoint.
Secure Your File Movement with GoAnywhere
Start a free 30-day trial and see if GoAnywhere is the right solution for your organization.