Secure Custom-Made Forms
Secure Forms allow your end-users to fill out and submit information online through secure custom-made forms with one or more input values, optionally upload files through GoAnywhere's HTTPS Web Client, or submit forms online by making SOAP or REST requests from your custom built applications.
When a form is submitted, a Project in GoAnywhere is executed to automatically process the submitted values and files.
Why Use Secure Forms?
To control the data that end-users provide when submitting information, GoAnywhere administrators can define Secure Forms with:
- Configurable input fields
- Custom labels
- File upload components
When the Project processes the Secure Form, it can return a custom message and one or more output files to the user.
A Secure Form can be specified to various intended languages. For example, two forms may be created that serve the same purpose, but one may be in French while the other is in English. GoAnywhere administrators can choose their preferred language in the Web Client, which will then only show forms that are applicable to the selected language.
Secure Form Submission
A Secure Form can be authorized to one or more Web Users, who must then log in through the Web Client to complete the form. Optionally, Secure Forms can be configured to allow anonymous users to access the form through a public URL.
Secure Form Use Cases
Secure Forms are used by organizations in all industries to streamline, centralize, and standardize information intake. Companies have used Secure Forms to reduce the number of ways in which files arrive (i.e., by fax, email, or other online submission), collect confidential information, and ensure data is delivered securely.
In one instance, Secure Forms are used to collect electronic voting ballots by prompting the user to enter their voting information and attach a scanned PDF. A Project workflow then automatically process and distribute this electronic ballot to the appropriate election official based on the voting information provided by the end-user within the Secure Form
Secure Ballots Made Easy
Secure Forms Features
- Custom, fillable Secure Forms for either public or authenticated users
- Flexible configuration and design options to control the position of form features such as buttons
- Customize and control the input text, options, and dropdown fields with default values, tooltips, and placeholders
- Projects that automate processing the Secure Form input data and, optionally, provide output messages and one or more files for users to download
- Fully customizable Text Area components, including the ability to override the button labels, the characters remaining text, and the drop zone on File Upload components
- Successful submission messages presented to users when Secure Forms are submitted
- Drag and drop upload for files which are automatically secured with AES-256 bit encryption
- Limit file upload parameters, including the file types that are permitted to upload, file size, and maximum number of files
- Save drafts of Secure Forms to finish at a later date
- View Secure Form submission history, including when the form was completed, the user who completed the form, the user’s responses, and more
- Supports SOAP and RESTful Web Service APIs to allow you to submit forms from other applications
Example Secure Form:
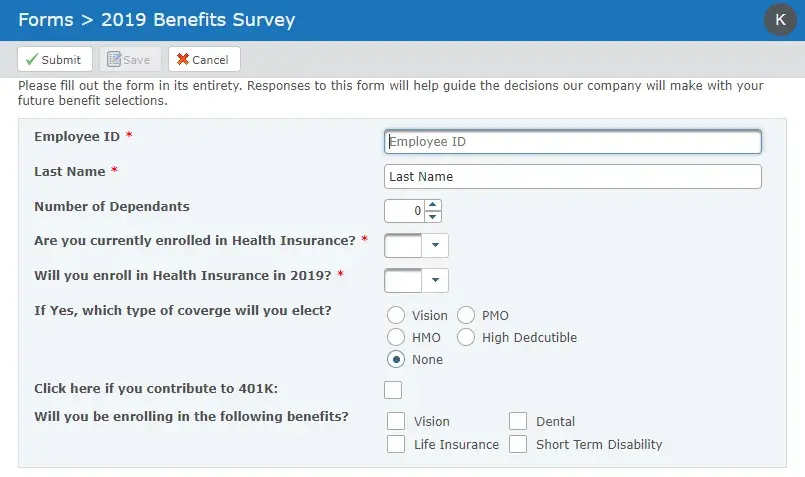
Improve Collaboration with GoAnywhere MFT and Secure Forms
Request a quote for Secure Forms in GoAnywhere MFT